Security and Management
The Aserto Control Plane can be used to control certain operations on running Edge Authorizers. For example, one can list running Edge Authorizers and issue policy and directory sync commands. This link between the Aserto Control Plane and Edge Authorizers requires setting up a secure connection between the two.
Edge Authorizer Connections
Edge Authorizer connections can be created from the Aserto console or API and provide an identity that Edge Authorizers can use to connect to the Control Plane. Edge Authorizers can use this identity by presenting a client certificate; performing a mutual TLS handshake. This identity is only authorized to establish a connection to the Aserto Control Plane for the purposes of receiving control commands and uploading decision logs.
Edge Authorizers use one of these identities by presenting the client certificate associated with a given authorizer connection. All authorizers presenting the same client certificate use the same identity and there can be as many Edge Authorizer connections as needed.
Once an Edge Authorizer is connected to the Aserto Control Plane:
- It will automatically refresh its policy state when a new policy image is pushed.
- It will automatically refresh its policy state when the policy instance changes.
- It can receive remote commands to refresh its policy and directory state.
- Its ability to connect can be revoked by deleting the Edge Authorizer connection from which its client certificates were obtained.
Configuration
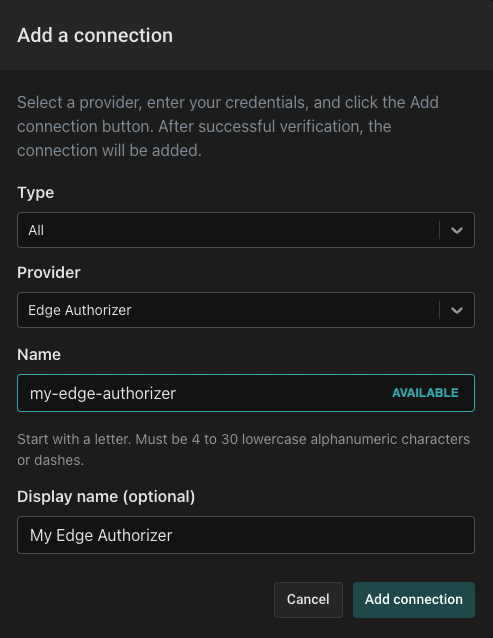
To use an Edge Authorizer, you'll first need to create an Edge Authorizer connection. Head to the Connections tab, and create a new connection by clicking the "Add connection" button. Select the "Edge Authorizer" and provide a name and a display name for your authorizer connection.
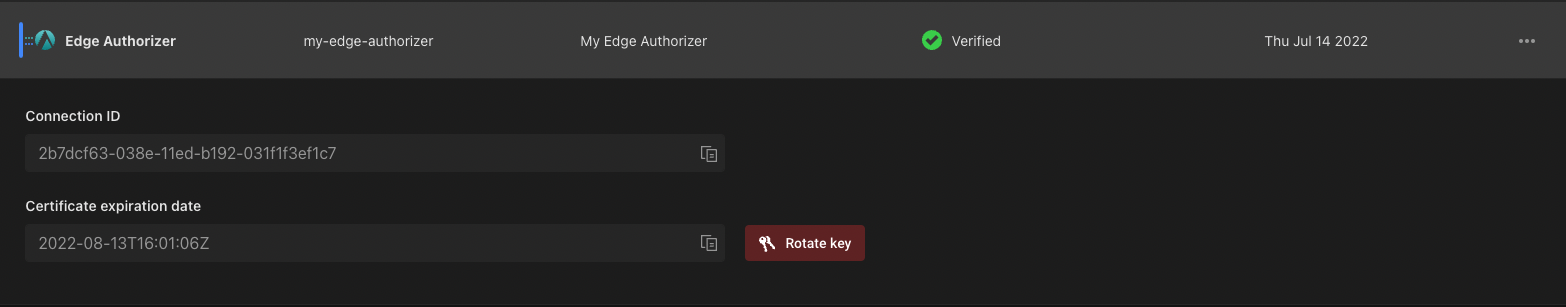
Click on the newly created connection to retrieve the Edge Authorizer Connection ID, which will be used to configure the Edge Authorizer.
Connecting to the control plane
The Aserto CLI can then be used to configure the Topaz instance to use the Control Plane by adding an option to the aserto config new sub-command. This will install the client certificates and configure the authorizer to connect to the Control Plane using them.
An authorizer can also be configured to generate decision logs and upload them to the Control Plane. To do this add the --decision-logging argument.
Obtaining certificates
Certificates have a lifetime of 30 days. You can rotate the certificates in the Aserto console. To obtain the new client certificates, issue the following command using the Aserto CLI:
aserto control-plane get certificates <edge-authorizer-connection-id>
This will return a JSON object with data about the client certificate, for example:
{
"certificate": "-----BEGIN CERTIFICATE----- <elided data> -----END CERTIFICATE-----",
"common_name": "edge-test.69b537c3-8db5-11ec-8417-00c5cc9cb8c0.edge-authorizer.aserto.com",
"expiration": "2022-06-24T17:11:31Z",
"id": "2b:d0:75:a0:7f:25:e8:2d:75:3d:20:cd:f3:e7:0c:f6:8d:02:94:01",
"private_key": "-----BEGIN RSA PRIVATE KEY----- <elided data> -----END RSA PRIVATE KEY-----"
}
The certificate field contains the certificate in PEM format and the private_key field contains the private key, also in PEM format. The contents of these fields should be saved as two files, for example ~/.config/aserto/sidecar.crt and ~/.config/aserto/sidecar.key.
Using the paths in the example, the configuration file of an Authorizer can be updated to connect to the Control Plane by adding a section similar to:
tenant_id: <TENANT-ID>
policy_name: <POLICY-NAME>
instance_label: <INSTANCE-LABEL>
controller:
enabled: true
server:
address: relay.prod.aserto.com:8443
client_cert_path: ~/.config/aserto/sidecar.crt
client_key_path: ~/.config/aserto/sidecar.key
To also configure an Authorizer to upload decision logs, add the following config section:
decision_logger:
type: self
config:
store_directory: /app/decision_logs
scribe:
address: ems.prod.aserto.com:8443
client_cert_path: ~/.config/aserto/sidecar.crt
client_key_path: ~/.config/aserto/sidecar.key
ack_wait_seconds: 30
headers:
Aserto-Tenant-Id: <TENANT-ID>
shipper:
publish_timeout_seconds: 2