Discovery Flow
When a new Edge Authorizer is started, the discovery flow will be initiated:
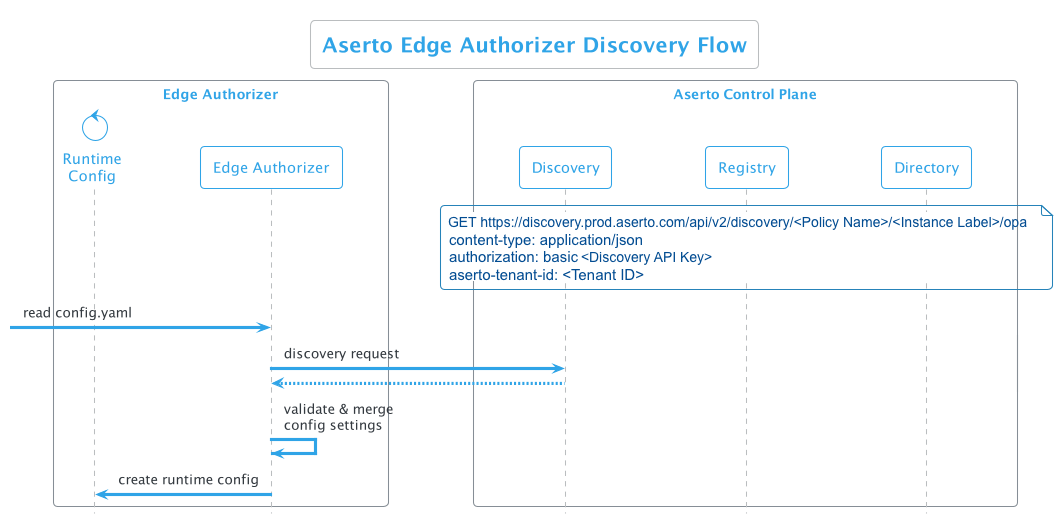
- A configuration file (config.yaml) is passed to the authorizer when it is started
- The authorizer makes a discovery call to the Control Plane, passing the policy name, instance label, authorizer API key, and tenant ID.
- The authorizer receives a response from the Control Plane including the configuration that the Edge Authorizer will need pointing it to the specific policy bundle.
- The authorizer validates and merges configuration settings
- Finally, the authorizer creates a runtime configuration
Configuration
To create the configuration file needed to bootstrap the Edge Authorizer, you can either the aserto CLI and then copy the config out of the ~/.config/aserto/sidecar/cfg folder or retrieve the credentials from the Aserto Console and use them in the configuration template found below.
Retrieving credentials from the Aserto Console
You can retrieve the configuration credentials from the console and copy them into the configuration file template found below.
- The discovery API key is located on the connections tab, under system connections. Click on the “discovery” connection to expose the information associated with the connection.
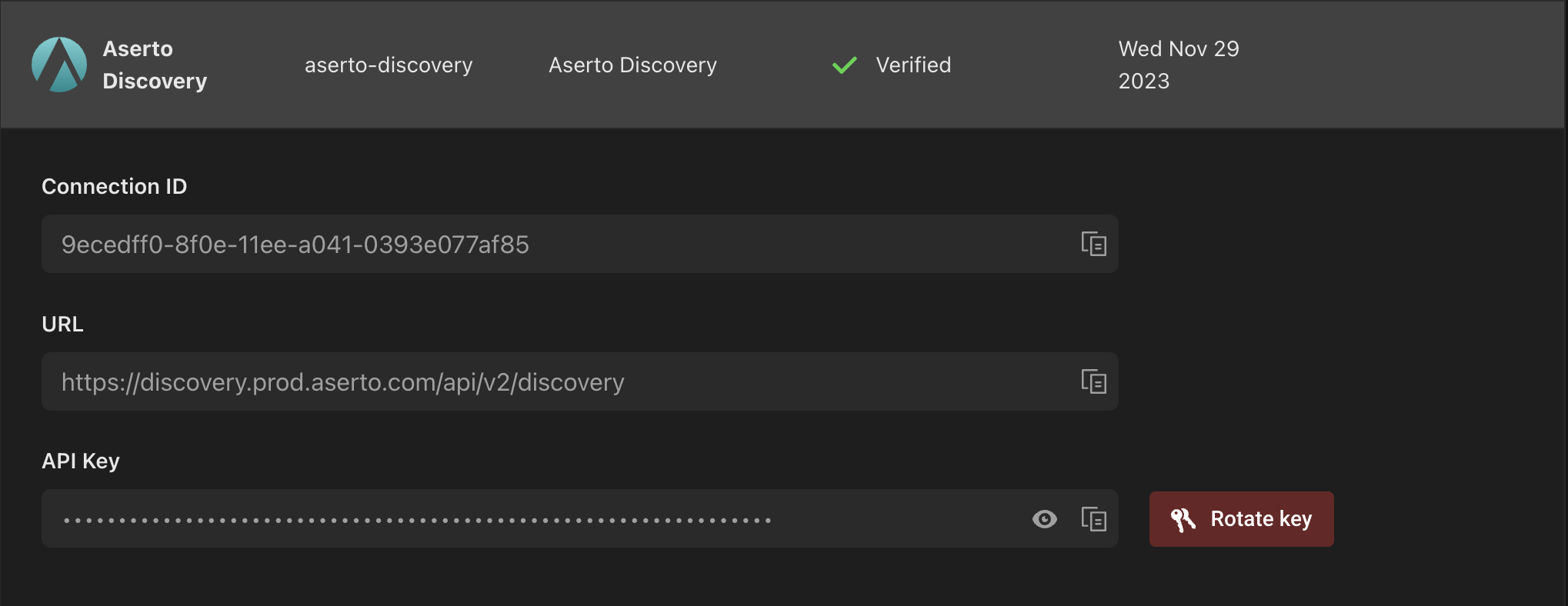
- The tenant and policy identifiers can be retrieved from the Policy Settings page of the policy instance which needs to get assigned to the Edge Authorizer instance.
These credentials map into the config.yaml file:
---
logging:
prod: true
log_level: info
directory:
db_path: /db/directory.db
api:
authorizer:
grpc:
connection_timeout_seconds: 2
listen_address: '0.0.0.0:8282'
certs:
tls_key_path: '/certs/grpc.key'
tls_cert_path: '/certs/grpc.crt'
tls_ca_cert_path: '/certs/grpc-ca.crt'
gateway:
listen_address: '0.0.0.0:8383'
allowed_origins:
- https://*.mydomain.com
certs:
tls_key_path: '/certs/gateway.key'
tls_cert_path: '/certs/gateway.crt'
tls_ca_cert_path: '/certs/gateway-ca.crt'
health:
listen_address: '0.0.0.0:8484'
opa:
instance_id: <TENANT_ID>
graceful_shutdown_period_seconds: 2
config:
services:
aserto-discovery:
url: https://discovery.prod.aserto.com/api/v2/discovery
credentials:
bearer:
token: '<DISCOVERY_API_KEY>'
scheme: 'basic'
headers:
Aserto-Tenant-Id: <TENANT_ID>
discovery:
service: aserto-discovery
resource: <POLICY_NAME>/<INSTANCE_LABEL>/opa
decision_logger:
enabled: false
Configuration Validation
To validate the correctness of the data used and to inspect what information is exchanged between the Edge Authorizer and the Control Plane, the following curl command can be used to execute the discovery request:
curl --request GET \
--url https://discovery.prod.aserto.com/api/v2/discovery/<POLICY_NAME>/<INSTANCE_LABEL>/opa\
--header 'Accept: application/json' \
--header 'Content-Type: application/json' \
--header 'aserto-tenant-id: <TENANT_ID>' \
--header 'authorization: basic <DISCOVERY_API_KEY>'
The expected response should be:
{
"opa": {
"discovery": {
"bundles": {
"<POLICY_ID>": {
"persist": false,
"polling": {
"max_delay_seconds": 120,
"min_delay_seconds": 60
},
"resource": "<TENANT>/<POLICY>//blobs/sha256:<DIGEST>",
"service": "<CONNECTION-ID>-tenant",
"signing": null,
"size_limit_bytes": 0
}
},
"plugins": {
"aserto_edge": {
"addr": "directory.prod.aserto.com:8443",
"apikey": "<REDACTED directory API key>",
"enabled": false,
"insecure": false,
"page_size": 100,
"sync_interval": 60,
"timeout": 10
}
},
"services": {
"<CONNECTION-ID>-tenant": {
"credentials": {
"bearer": {
"token": "<REDACTED> registry download API key"
}
},
"response_header_timeout_seconds": 60,
"url": "https://registry.aserto.com/v2/"
}
}
}
}
}
When the Edge Authorizer receives the discovery response, the information received will be replace the OPA element from the bootstrap configuration, resulting in the following configuration.
The Edge Authorizer runtime configuration is ephemeral and does not get persisted to disk.