Quickstart and Modules tabs
Click on the api-auth policy instance, and select the Quickstart tab. The Citadel identity provider that contains the Rick and Morty users is already connected.
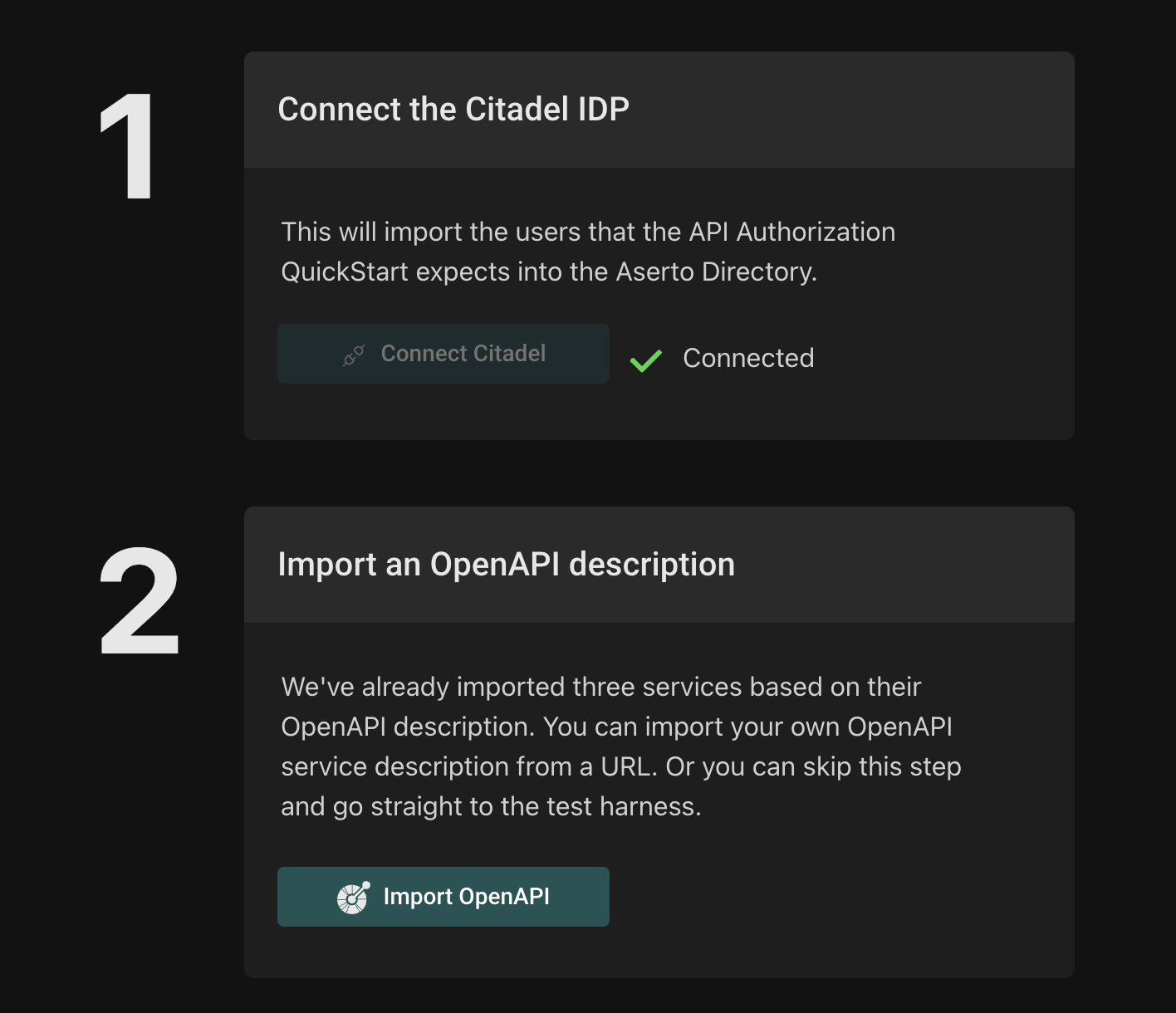
Import an OpenAPI spec
In the next step, you can optionally import your own OpenAPI spec. If you have one ready, try it out... otherwise feel free to skip this step and rely on the existing three services that we’re using as sample data.
The OPA policy
Click on the Modules tab, and observe a single Rego module - the boilerplate policy-rebac.check module.
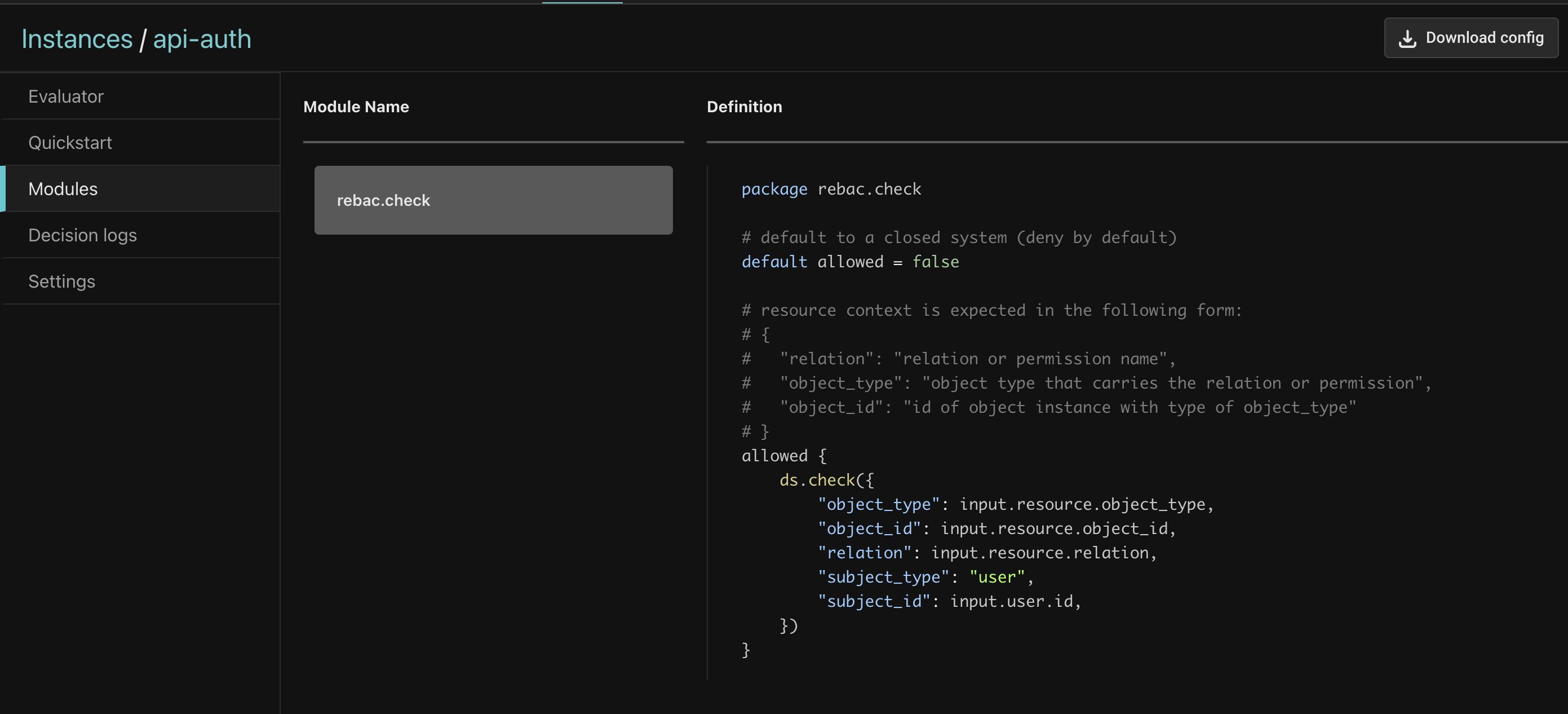
Compare that with the complexity of having to manage a custom policy for every service! As mentioned, we are transforming a policy problem into a data modeling problem, which we will explore next.
But it’s important to note that any additional attribute-based access control or environment-oriented access restrictions can be easily added to this boilerplate policy. For example, you can easily extend the policy to ensure that users who are “contractors” are only allowed to invoke endpoints on weekdays.
Since every OPA policy is a Topaz policy, you can bring the full power of OPA and Rego to bear on your custom authorization policies.
Next steps
Next, let's explore the authorization model and the instance data that the template created.