Sign in to a registry
Just like with docker login, the policy CLI requires you to sign in to an OCIv2-compliant registry.
echo $PAT | policy login -s <server> -u <username> --password-stdin
Options
-s <server>: container registry address
-u <username>: username / account
-p <password>: password or a PAT
--password-stdin: read the password from stdin
Aserto Policy Registry
Aserto provides a built-in policy registry. To sign in to the Aserto Policy Registry (APCR), you'll have to retrieve your APCR API key. Head to the "Connections" tab, and click on "APCR":

Click the "Copy" icon next to the "API Key" field.
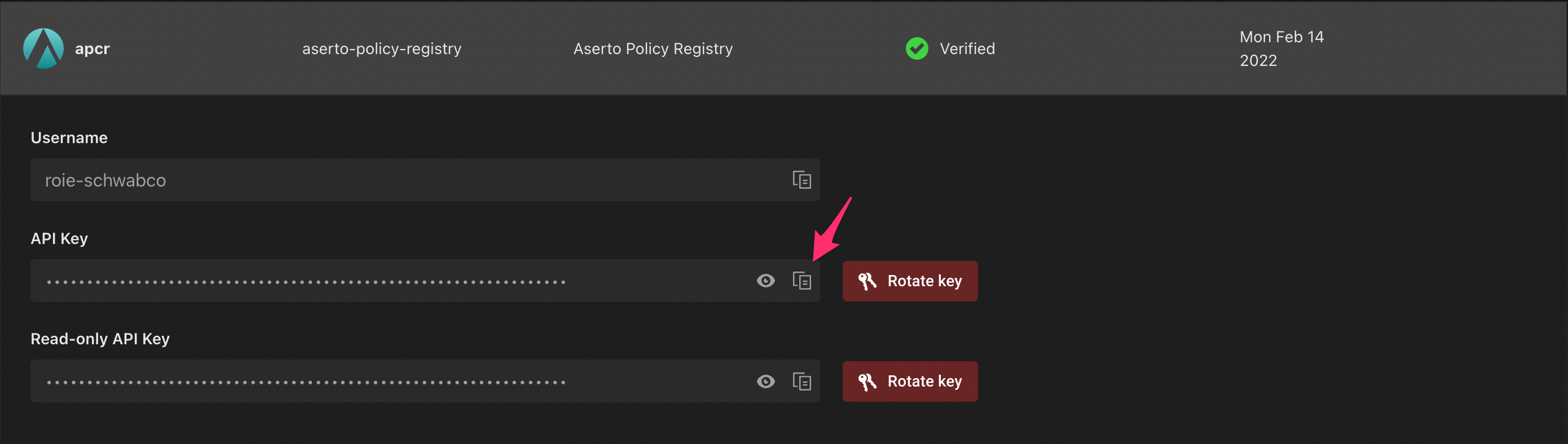
Then head back to the terminal::
policy login -s registry.prod.aserto.com -u <Aserto-Username> -p <APCR-API-Key>
Other container registries
The policy CLI supports any OCIv2-compatible container registry as a policy registry. Below are examples for how to use policy with various registries.
AWS Elastic Container Registry
AWS ECR credentials to authenticate can be obtained using the AWS CLI command aws ecr get-login-password.
aws ecr get-login-password |policy login -s <org>.dkr.ecr.<region>.amazonaws.com -u AWS --password-stdin
Create a new policy repository:
aws ecr create-repository --repository-name <my-policy-name>
This will return a URI to push policy images to.
GitHub Container Registry
To sign in to the ghcr.io registry, use your GitHub account, and a GitHub personal access token (PAT) as your password which contains the appropriate scopes - for example, repo (required), read:org (for organizations), write:packages, and delete:packages.
echo $PAT | policy login -s ghcr.io -u <username> --password-stdin
You can create a GitHub PAT on this page.
Docker Hub
You can use your password or a PAT to login to Docker Hub:
echo $PAT | policy login -s registry-1.docker.io -u <username> --password-stdin
Google Container Registry
Follow the steps to authenticate to GCP here.
For example, create a JSON key file for a service account using the following command:
gcloud iam service-accounts keys create keyfile.json --iam-account [NAME]@[PROJECT_ID].iam.gserviceaccount.com
Then login using policy the same way you would login to docker:
cat KEY-FILE | policy login -s gcr.io -u _json_key --password-stdin
Docker credential helpers
Version 0.2.0 of the policy CLI adds support for docker credential helpers to securely store credentials. Credential helpers are configured in ~/.policy/config.json.
Login credentials that were saved with previous versions of the policy CLI will need to be updated.
On Windows
To use the credential manager on Windows:
- Install the wincred binary into a directory in your $PATH.
- Edit
~/.policy/config.jsonto setwincredas the credential store:
{
"auths": {},
"credStore": "wincred"
}
- Log in with the policy CLI.
Your credentials are now securely stored with Windows Credential Manager.
On MacOS
- Install
osxkeychainfor amd64 or arm64 into a directory in your $PATH. - Edit
~/.policy/config.jsonto setosxkeychainas the credential store:
{
"auths": {},
"credStore": "osxkeychain"
}
- Log in with the policy CLI.
Your credentials are now securely stored in your MacOS KeyChain.